Introduction to Software Development Process
The appropriate development of the software process and their usability in the market will help to get the information about the entire process as the software development process gone through with various lifecycle process. The modern software development procedure and it will face the several steps to place itself in the final stage. There are some hazards that the process faces. Thus an occurrence being the assault that exploits helplessness by understanding a danger. One of the points of secure advancement (aside from building programming frameworks) is to recognize and relieve dangers before they wind up noticeably exploitable vulnerabilities underway frameworks.
Programming designing as a train is as yet developing, so it is not nonsensical that protected improvement is still in its early stages. Most programming is shaky, as per Shostack and Stewart (2008). This could be on the grounds that, as (Pawlak et al. 2015) note, security prerequisites are frequently excluded from necessities details by and large. Security-situated programming improvement procedures are an undeniable parameter to target and solve this issue. A general announcement includes some of the software related programs. Similarly, in consideration to the powerful philosophy, none has tried the process, yet the way that these strategies put security necessities to the requirement areas and at the vanguard of all phases for their particular improvement lifecycles need to outcome in better way (more secure, along these lines more useable) frameworks, provide philosophies, that have a sound hypothetical supporting and that they are connected accurately by the professionals).
The security necessities can be fulfilled by the help of the case of abasement. The study will evolve out the contrast of UML utilize process and abuse activity, clarifies the linguistic structure and semantics of abuse files by case, utilizes contextual analysis to show the abuse in adequacy of cases and finishes up with a thinking process about some of the shortcomings in the system.
UML Use Cases
Utilize procedures were initially announced by (Huang et al. 2015) and have been a piece of the UML standard since its origin (maybe obvious, as Jacobson, being the one person who belongs "three amigos" of the UML group). A utilization process is "a portrayal about an arrangement of groupings activities that incorporate variations that a framework plays out to supply a perceptible aftereffect about the significant worth to a performing artist" (Uebe et al. 2015). In this manner, an utilization case is an abnormal state, client centered depiction of what a framework will do which serves to characterize the extent of the framework, hence utilize cases are firmly bound to prerequisites. Utilize cases are frequently communicated in an outline yet the truth be told, printed portrayals of procedures. A utilization case chart comprises of utilization process (spoke to by the ovals) encompassed by a framework limit with on-screen characters outside the framework following it up to start forms (utilize process). A utilization case chart gives data about the real usefulness of a framework, which is empowered to play out that usefulness and connections between the capacities. The connections are of four sorts, viz affiliation (performing artist/performer), consideration (utilize case/utilize case), expansion (utilize case/utilize case) and speculation (on-screen character/on-screen character or utilize case/utilize case).
A Use Case Diagram
In the framework the main criteria revolves around the films that get covers in a nation and based on the requirements and it also connected and collaborate with the silver screen rooms along with the proper arrangement of seats in those rooms. Other than that the rooms can be structure and design in a way so that it can able to view from the online silver screen administrative structure. This efficient and effective design method will provide the purpose for the way, so that the future discharges can process with the help of the existing framework process.
The framework get utilized in various ways one of the most effective one being the individuals will go through the frame works to invent the motion picture session and this session will also adjoin city, region, nation and time. If someone penetrate in the site page framework then the entire processing related to the neighborhood hunt condition will open up with the insight of period intern spreading over. During the entrance of a client, that individual will get numerous options related to session-connections that will deliver fulfillment regarding the rundown-overview. In the session interface, it provides a graphical introduction about the session rundown and their seats can be chosen by the individual of their choice and they can also follow the booking criteria as the prize will pop-up on the session as an aggregate price. The booking number will also viewed on the screen as the process will get confirmed and the client will get that proof and for the booking, later he can takes out the print invoice. After this entire procedure the client can face some of the difficulties and in case he wants his cash back then with the help of the printing invoice he can claim to get back the money and session –cancellation. If the procedure get interrupted before he finalize his own seat then his seat will get cancelled and it will cross over to the different clients and the next client will get the chance to book the ticket. Later the thing can be fixed by the help of the process that the director will help to set up the motion picture. The data for that session will keep beside to fulfill the demand of any client later. The web printer will help to take out the tickets that is more convincible and can able to secure the entire framework process. The printing invoice will be the proof to solve the problem regarding any of the client’s obligations.
Assumptions and Risks
Assumptions
- Resources (hardware, software, and people) are available to use upon request
- There will be no costs incurred by the Center for Project Excellence
Constraints
- Time of developing the system since we are running on a school semester time period
- Trainers and developers for the system because there is a limited number of people working for the CPE
Feasibility Assessment
To design the new system that will meet the needs of the Center for Project Excellence, a business case that justifies the expenditure of resources on the project is needed. This is needed in most projects because it allows us to evaluate a wide range of factors. Our group is fortunate enough to report that our project for the CPE has been found feasible. The results are explained below.
Economic Feasibility
By identifying the financial benefits and costs of this new system, one can take up the acknowledgement and understanding of the economic analysis of this project. The economic benefits of creating this system rely more on the intangible benefits rather than the tangible because there is technically no budget for this system and the development is all on a volunteer basis. This makes it more economically feasible because there are not many budget constraints within this system. If this system is approved it has a good opportunity to have a positive effect on the CPE and the way it conducts business between companies.
Technical Feasibility
The framework will have a database and UI for the clients of the framework to information. The clients of the framework are knowledgeable on utilizing data frameworks and won't require a considerable measure of preparing. The University Of Dayton School Of Business gives the Center to Project Excellence with enough equipment and programming innovation to execute and utilize this framework. Likewise, the clients of the framework are taught enough that base preparing is required while executing the framework.
Operational Feasibility
The mission of the Center for Project Excellence is to join hypothesis with practice. They are having understudies draw in with genuine organizations on genuine activities. The middle is hoping to develop by going up against more undertakings and keep on taking on ventures that are long haul and require understudy inclusion outside of the scholastic year. By actualizing this new framework, the CPE will have the capacity to match understudies with ventures quicker which will prompt the inside's capacity to go up against more tasks. The framework will be organized and give a composed method for getting to data and contributing information. By having an organized database of data on understudies and undertakings, the middle can develop and keep on becoming an all around statured fixate on grounds.
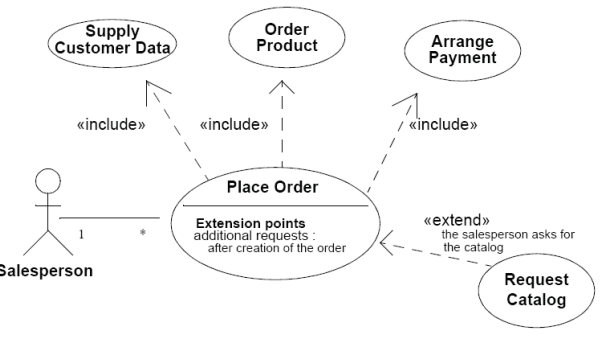
Affiliation associates performing artists to utilize cases. In this case, a sales representative can put in many requests. The «include» generalization encourages reuse of basic usefulness, like the way the volume and potentially of the call works in programming, so as a major aspect to the "Place Order" utilize process, the "Supply of the Customer Data" utilize process will be summoned. The generalization procedure permits discretionary conduct, like choice or conditionals in programming, hence as a feature of the "Place Order" utilize case, the "Ask for Catalog" utilize case might be conjured. Speculation (not appeared on figure 1) permits IS-A connections to be portrayed e.g. a Salesperson is a worker or "Pay with charge card" is an approach to "Mastermind Payment". On-screen characters can be parts played by people, different frameworks or equipment gadgets. UML form 2 (OMG, 2007) considers other on-screen character symbols for instance, different symbols that pass on the sort of performing artist may likewise be utilized to indicate an on-screen character, for example, utilizing a different symbol for nonhuman on-screen characters, however this utilization seems, by all accounts, to be genuinely remarkable by and by and on-screen characters do not consider about their characteristics and have a tendency to spoke to as stick figures. Having given some fundamental points of interest of the utilization case outline procedure, the following area presents abuse occurrence as a security-arranged simple of utilization process.
Misuse Cases
While utilize occurrence are useful for the inspiration of practical necessities, they do little for non-utilitarian prerequisites (which the security prerequisites being a sub-class). (Sindre and Opdahl 2012) portray an abuse files as the reverse of an utilization process, i.e., a capacity that the framework will not concern and permit… one could characterize an abuse case as a finished arrangement of activities that brings about misfortune for the association or some particular partner." Additionally, "A miss-performer is the opposite of an on-screen character, i.e., an on-screen character that one doesn't need the framework to bolster, an on-screen character who starts abuse files." In conjunction with the ideas of abuse files and miss-on-screen character (once in a while called a misuser), (Sindre and Opdahl 2012) likewise suggest additional generalizations, viz: «prevents» and «detects», to help in demonstrating security connections. For instance, an "Encode message" utilize case avert "Tap interchanges" abuse case and a "Screen framework" utilize case «detects» a "Get secret key" abuse case (see figure 2). In an abuse case outline, the abuse files and mis-on-screen characters have delineated to reverse hues for the recognition from traditional utilize process along with the performers.
As suggested by (Yin et al. 2014) seems too disposed of these generalizations for «threatens» and «mitigates». Similarly that a utilization case can incorporate other, an abuse case may likewise «include» the usefulness of another abuse case. It may not, nonetheless, be clear that the connections between utilize cases and abuse files are an) an utilization case can «mitigate» an abuse case; and b) an abuse case can «threaten» an utilization case. Other work on abuse files incorporates explains on the unobtrusive refinement between abuse files and security utilize cases. The previous are, obviously, about determining what happens when a miss-performing artist succeeds, while the last are worried with guaranteeing that the framework succeeds (or rather the mis-performer does not). Firesmith would state that "Execute misrepresentation" is an abuse case (since it is performed by a miss-performer, with the point of misusing a framework) while "Guarantee non-revocation" is a security utilize in light of the fact that it «mitigates» the "Execute extortion" utilize case. The possibility of security utilize cases is likewise upheld by (Tanaka and Inui, 2016), likewise recognizes the contrasting reasons for abuse files and security utilize cases in that while abuse files can be a compelling strategy for investigating dangers, they ought not to be utilized for determining (security) necessities since security prerequisites are about giving assurance from dangers. This partition amongst risk and relief is found in figure 3, where abuse files drive security utilize process.
Alexander (2003) brings up that extreme security controls may damage access to the authentic clients related to the framework and proposes «bother» and «conflicts with» as expansions to model associations with the level of control that is necessary for the whole process. (Ravindran and Tsai 2016) bolster work on the abuse files however express that security is a significant.
Thing and a product highlight and in this manner can't be included into the framework as an idea in retrospect. They contend that security must be considered at venture initiation. While this is an excellent point, numerous product engineers realize that the expansion of security capacities change the degree, timing and costing of a venture and such capacities might be left unimplemented as an item sending date looms, particularly as security prerequisites are not as unmistakable as practical necessities. This sort of conduct is worried with conceding hazard as noted by (Ojha et al. 2016). In looking at SDL, CLASP and TouchPoints, De Win et al. (2008) take note of that CLASP takes both a dark cap and a white cap point of view, it uses abuse files and recognizes protection components for those abuse files, accordingly producing security prerequisites as talked about by (Mehta et al. 2014) specify that SDL does not use abuse files, but rather there is no reason that they can't be incorporated into SDL as will be found in the second area.
Implementation of Misuse Cases: Related to a Case Study
Contextual analysis utilized in that portrayed by (George et al. 2015) that is basically is an online business framework for a shop that permits clients buy merchandise from Internet. Clients might be individual or unknown clients. Requests might be put and paid-for quickly or conceded. On the off chance that the merchandise requested are not in stock then a delay purchase is raised yet the client is not charged until the products are delivered. Howard and Lipner adjusted the first contextual investigation marginally to incorporate a review log. For effortlessness, the particular territory of the case that will be centered around is the request preparing framework. Different on-screen characters, for example, the anonymous user and administrator will disregard as the additional utilization process required to handle conceded orders. Utilizing this pet shop web based business study, the main performers and procedures were distinguished, along these lines producing a traditional utilize case outline (figure 4). The method was then stretched out to cover abuse files by considering likely security dangers (figure 5). Despite the fact that figure 5 is adequately just a fractional abuse case chart (as it contains just a solitary abuse case fixing to prepare an installment), it is in any case educational. What is fascinating about figure 5 is that it was really made in a two-organize prepare. To begin with, the misuser or the hacker and abuse files were brought into figure 4 (the utilization process graph). Utilize process are about fruitful fulfillment of the abuse files are adequately reverse of utilization process (they behave to upset the framework somehow), so to the second stage the security utilize case.
When you begin a web application outline, it is basic to apply risk displaying; else you will waste assets, time, and cash on futile controls that neglect to concentrate on the genuine dangers. There are various ways to deal with danger demonstrating, as recorded beneath:
- Programming driven risk demonstrating
- Security driven risk displaying
- Resource or hazard driven risk displaying.
The technique used to evaluate hazard is not so essential as really playing out an organized danger chance demonstrating. Microsoft noticed that the absolute most critical figure their security change program was the corporate appropriation of danger hazard demonstrating. One of numerous contemplations is Microsoft's risk demonstrating process. It is easy to receive by planners, designers, code analysts, and the quality confirmation group. The accompanying areas give some outline data (or see Section 6.9, Further Reading, for extra assets).
Discussion and analysis
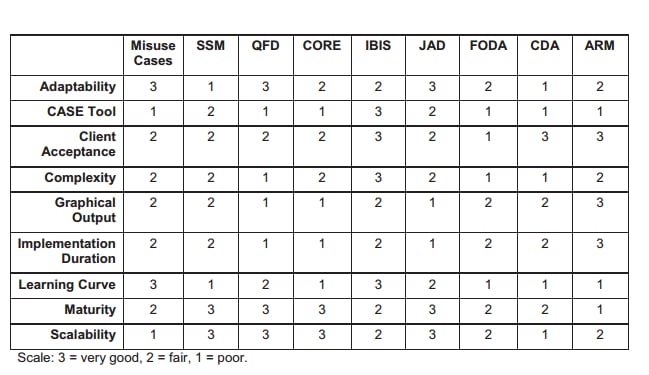
(Fotrousi et al. 2014) assessed scope for the prerequisites selection methods, and the abuse arguments contrasting positively against most of alternate strategies, particularly based to the regions for versatility, simplicity of learning (see table 1). Possible proof from the contextual analysis and table 1 proposes which producing abuse files (and related security utilize process) is a moderately clear assignment, truly it is not connected.
To solve the matter regarding the misuse cases need to consider various process and the first process will be the care and guidance moreover getting the knowledge of the cases so that it can mitigate in small amount of time with better understanding and better insight. In regards to the security of the system area many decision can be made to solve this thing. The frustrated employees will not motivate themselves for work and they will continue to spread the negative result and it will proceed towards a bad circumstances. The employees need to distinguish themselves according to their work allotment so that they can solve any problem and to avoid any unwanted situation. The security control for the frustrated employees need to be stronger as they will want to break it anyhow and will not follow any rules. The internal mis-actors and the external mis- actors need to distinguish them so the processing become easy to handle. The misuse cases need to handle properly as there will be problem regarding ‘increase privileges’.
The interest mainly generate from the prospect that how to generate the misuse cases. The considered action oriented method will implement here and it will execute in the task processing with the help of the legislation process with the investigation opportunity for the same. The conventional way to engineering things will not be applicable here as they will not able to detect the policies and concern related to the mis-users of the system. The client interview will also not help because that individual can hide anything and can manipulate the authentic matters to a great extent. In such a case where the clients know about the entire matter and he is willing to provide the true answer then only can the matter proceed for further. Placing one person to the other will help to chalk out the matter very clearly as he will forecast things on the behalf on other person and the opinion of other person can be effective. The main drawback of the process being the engineer is not the hacker and by using this technique it will not see success and it will lead to vulnerabilities and the person who is closely related to that process can notice compulsion. The design patter of that software needs to be so strong so that the hacker cannot able to hack the process and it can work appropriately. The experience based solution for the design will help the software to save itself from any vulnerability and the requirements of the proper engineering process can be though this basis. The skill and the knowledge of the engineers will help the software to process in better way and protect itself from the hackers. The powerful pattern that the engineers will use will solve the problem for misuse files and the problem solving method will apply in the good software design patterns. The structuring need to be very much strong so that it can eliminate the misuse problem and it will come to the engineers with the help of the brain storming process. The STRIDE elements in this factor is a powerful considerate where with possible and best constructs will help to solve any matter related to misuse and it will further consider the security processing for the mitigation of powerful strategies.
If you want to learn more about engineering or other assignment help then, please visit instant assignment help Australia.
Conclusions and Further Work
As hacking is the big criteria in this respect and it not solve any how so the strategic and powerful implementation of the plans will help to generate goodness in the entire process. The understandable and simple technique is very much significant in this criteria and STRIDE will help to mapping up the techniques for the same so that all the threats can be eliminated from the section.
References
- Rogers, D.J. and Moore, M.A., Terbium Labs LLC, (2015). Systems and methods for detecting copied computer code using fingerprints. U.S. Patent 8,997,256.
- Pawlak, T. P., Wieloch, B., & Krawiec, K. (2015). Semantic backpropagation for designing search operators in genetic programming. IEEE Transactions on Evolutionary Computation, 19(3), 326-340.
- Huang, P., Deng, S., Zhang, Z., Wang, X., Chen, X., Yang, X., & Yang, L. (2015). A sustainable process to utilize ferrous sulfate waste from titanium oxide industry by reductive decomposition reaction with pyrite. Thermochimica Acta, 620, 18-27.
- Uebe, M., Ito, A., Kameoka, Y., Sato, T. and Tanaka, K., 2015. Fluorescence enhancement of non-fluorescent triphenylamine: A recipe to utilize carborane cluster substituents. Chemical Physics Letters, 633, pp.190-194.
- Yin, S., Ding, S. X., Xie, X., & Luo, H. (2014). A review on basic data-driven approaches for industrial process monitoring. IEEE Transactions on Industrial Electronics, 61(11), 6418-6428.
- Tanaka, Y. and Inui, T., (2016), September. Preliminary study on why university researchers do not utilize patent information for their academic research in the field of science and engineering in Japan. In Management of Engineering and Technology (PICMET), 2016 Portland International Conference on (pp. 1609-1618). IEEE.
- Ravindran, M.S. and Tsai, B., (2016). Viruses Utilize Cellular Cues in Distinct Combination to Undergo Systematic Priming and Uncoating. PLoS Pathog, 12(4), p.e1005467.
- Ojha, S., Acharya, S.K. and Raghavendra, G., (2016). A novel approach to utilize waste carbon as reinforcement in thermoset composite. Proceedings of the Institution of Mechanical Engineers, Part E: Journal of Process Mechanical Engineering, 230(4), pp.263-273.
- Mehta, P., Singh, S., Roy, D. and Sharma, M.M., (2014). Comparative Study of Multi-Threading Libraries to Fully Utilize Multi Processor/Multi Core Systems. International Journal of Current Engineering and Technology, 4(4).
- George, A., Scott, K., Garimella, S., Mondal, S., Ved, R. and Sheikh, K., (2015). Anchoring contextual analysis in health policy and systems research: a narrative review of contextual factors influencing health committees in low and middle income countries. Social Science & Medicine, 133, pp.159-167.
- Fotrousi, F., Fricker, S.A. and Fiedler, M., (2014), August. Quality requirements elicitation based on inquiry of quality-impact relationships. In Requirements Engineering Conference (RE), 2014 IEEE 22nd International (pp. 303-312). IEEE.












